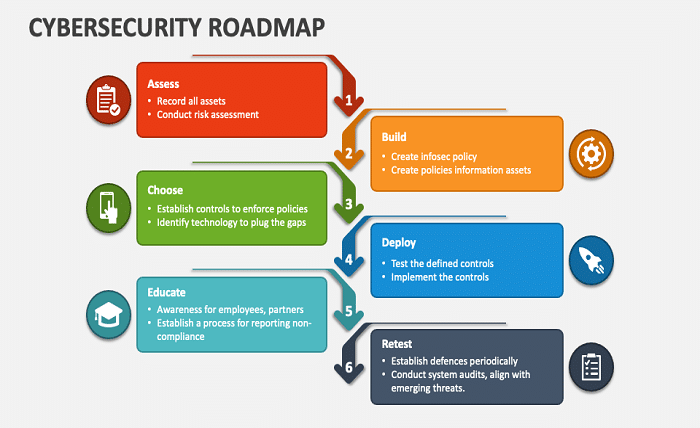
Digitally driven world, a well-defined cybersecurity roadmap is essential for safeguarding your organization’s data and assets. A cybersecurity roadmap outlines the strategic steps to protect against cyber threats, ensuring your organization remains resilient despite evolving challenges. In this guide, we’ll explore the critical components of a Cyberpublicity roadmap and provide actionable insights to help you create one that meets your specific needs.
Understanding the Importance of a Cybersecurity Roadmap
A cybersecurity roadmap is a strategic plan that helps organizations systematically address potential cyber threats. It ensures that all cybersecurity efforts are aligned with the organization’s objectives, providing a clear path to mitigate risks. Organizations may struggle to prioritize resources without a cybersecurity roadmap, leaving them vulnerable to attacks.
Assessing Your Current Cybersecurity Posture
Assessing your current cybersecurity posture is crucial before developing a cybersecurity roadmap. This involves evaluating your existing security measures, identifying potential vulnerabilities, and understanding the risks specific to your organization. Doing so lets you pinpoint the areas that need improvement and sets the stage for a more effective roadmap.
Defining Your Cybersecurity Goals and Objectives
Clear goals and objectives should drive a cybersecurity roadmap. These goals include reducing the likelihood of data breaches, improving incident response times, or ensuring compliance with industry regulations. Defining these objectives early on will guide the development of your cybersecurity roadmap and ensure that it addresses your organization’s unique needs.
Identifying Key Cybersecurity Risks
Identifying key cybersecurity risks is a critical step in developing your cybersecurity roadmap. These risks can vary depending on your industry, the size of your organization, and the nature of your operations. Common hazards include phishing attacks, ransomware, and insider threats. By identifying these risks, you can tailor your cybersecurity roadmap to address your organisation’s specific challenges.
Prioritizing Cybersecurity Initiatives
Once you’ve identified the key risks, the next step in your cybersecurity roadmap is prioritising initiatives to mitigate these threats. Prioritization should be based on factors such as the potential impact of a security breach, the likelihood of occurrence, and the resources required to address each risk. A well-prioritized cybersecurity roadmap ensures that your organization focuses on the most critical areas first.
Establishing a Cybersecurity Governance Framework
A cybersecurity governance framework provides the structure and oversight needed to implement your cybersecurity roadmap effectively. This framework should include clear roles and responsibilities, reporting mechanisms, and policies that guide decision-making. Establishing a robust governance framework ensures that your cybersecurity roadmap is executed efficiently and all stakeholders align with your security objectives.
Developing a Cybersecurity Training Program
Human error is one of the leading causes of security breaches, making employee training a vital component of any cybersecurity roadmap. A comprehensive training program should be developed to educate employees about cybersecurity best practices, recognise threats, and what to do during a breach. Regular training sessions should be scheduled to update everyone on the latest security protocols.
Implementing Advanced Security Technologies
Technology plays a crucial role in any cybersecurity roadmap. Implementing advanced security technologies, such as firewalls, intrusion detection systems, and encryption tools, can significantly enhance your organization’s defences. It is essential to choose technologies that align with your cybersecurity goals and can be integrated seamlessly into your existing infrastructure.
Regularly Reviewing and Updating the Cybersecurity Roadmap
A cybersecurity roadmap is not static; it must be regularly reviewed and updated to remain effective. Cyber threats constantly evolve, and your organization must adapt to these changes. Regular reviews will help you identify areas where your cybersecurity roadmap may need adjustments and ensure your organization is always prepared for new challenges.
Measuring the Success of Your Cybersecurity Roadmap
Finally, it’s essential to measure the success of your cybersecurity roadmap. This involves tracking key performance indicators (KPIs) such as the number of detected threats, response times, and the overall reduction in security incidents. By measuring these metrics, you can assess the effectiveness of your cybersecurity roadmap and make data-driven decisions to enhance your security posture further.
Conclusion
Creating a cybersecurity roadmap is critical in ensuring your organization’s long-term security and resilience. By understanding your current cybersecurity posture, setting clear objectives, and regularly updating your roadmap, you can stay ahead of emerging threats and protect your valuable assets. A well-crafted cybersecurity roadmap mitigates risks and empowers your organization to respond effectively to cyber incidents.
Read More:
Powering student-centric education in universities & collegesWe help universities and colleges of all sizes and streams run better – from admissions to academics, back office to accreditations, desktop to mobiles – We empower students, faculty and management to collaborate efficiently and use insights effectively, benchmarking quality education while creating personalized learning experience gu icloud